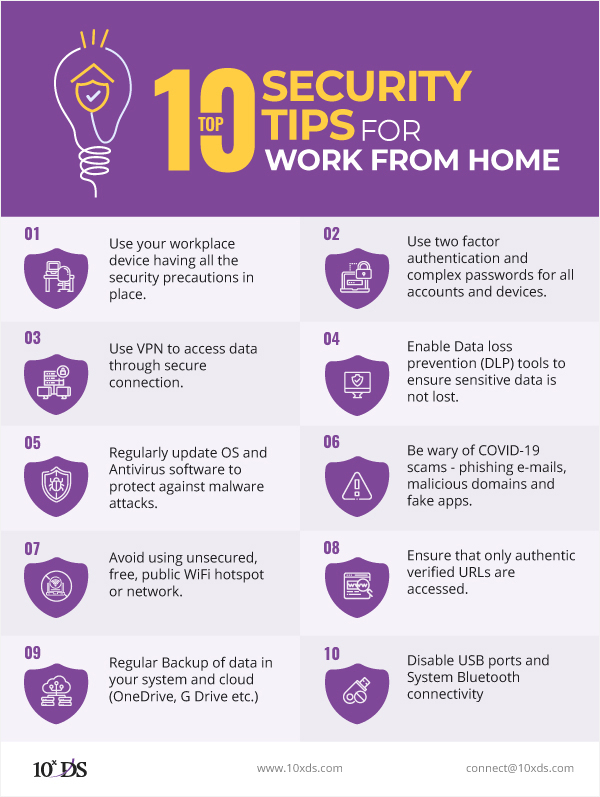
Top 10 Security Tips for Work From Home amid COVID-19 Lockdown
Amid the Novel Coronavirus outbreak across the globe, a sizeable majority of people are working from home. This can create some problems when it comes to the security of your systems, as you are working outside the office environment. Agreed, your IT Support team might be monitoring 24×7 to avoid any security issues, there are some things you as an individual can do to better secure your systems. Considering the situation, it is evident that working from home has become a new reality for people around the world, so its best to follow and ensure necessary security practices.
We have come up with Ten useful tips you need to remember and follow while working from home.
1. Use the workplace device
No words can adequately emphasise the importance of this tip. There is a general tendency to use both your laptops- the work one and your personal one – as per your convenience. This may be a huge mistake if you do not have necessary security features enabled in your personal device. So, it’s always best to use your workplace device while working from home, for your office work related purposes. Most workplace devices have pre-installed and functioning security precautions configured by your organization’s IT Support team. So, it’s best to avoid unnecessary risks by using your personal laptop as you will be a lot more secure while using the company given one. One more important thing, even if it’s for something very casual and small, never ever let other people borrow your company given laptop.
2. Use multi factor authentications
Multi Factor Authentications gives additional layer of security to ensure that the system is not compromised easily. In case malicious attackers happen to crack your username and password, then instead of immediately gaining access to your system, they are required to enter another security information to successfully hack into the system. It is always best to make sure that you use long, complex alpha numeric passwords and never ever reuse the same credentials across different platforms, it’s a huge security risk because if one account is compromised there is every chance all your other accounts may get compromised.
3. Use VPN to access data through secure connection
Try to ensure you are using a virtual private network (VPN) and this is critical while handling and accessing sensitive data as it provides secure connection to work files or personal data stored in the cloud. To put it more simply there is a virtual encrypted tunnel being created between you and a remote server operated by a VPN service. Everything you search and all the traffic will be routed via this tunnel, making your data is secure.
4. Enable Data loss prevention (DLP) tools
Data loss prevention (DLP) is a set of technologies, tools and processes used to ensure that sensitive information does not leave from an organization by losing it, being misused, or being accessed by unauthorized users. What the process and tools used to ensure the data security does is that information is classified as regulated, confidential and business critical. Then policy violations as defined by organizations are assessed as per the regulatory compliance requirements of GDPR, PCI-DSS, HIPAA, or any other specific to the organization, industry or region. After identifying the violations, the DLP process is initiated with alerts, and other security level actions to protect and prevent users from sharing sensitive data. These strategies usually include monitoring, detecting, and blocking the unauthorized access and information flow in an organization.
5. Regularly update OS and Antivirus software.
You might get these little pop-up windows telling you or reminding you to update the software in your system – OS, Antivirus software and others. Especially if it’s an OS or an Antivirus update its better not to click on the “Remind me later” button. Putting off updating your software for long can put your system at risk. Updates are important from a safety and cybersecurity perspective. The updates might have fixes for repairing security holes or computer bugs. Moreover, there might be new features being added or outdated ones removed. You should always check whether your operating system is running the latest version and if not upgrade to the new one.
6. Be wary of COVID-19 scams – phishing e-mails, malicious domains and fake apps
COVID-19 pandemic and related news have been getting the maximum coverage and now this is creating a new and different kind of danger — hackers and malicious cyber attackers are taking advantage of the pandemic by sending fraudulent emails, attempting phishing attacks looking to exploit public fears about the virus. The emails or messages trick you into opening the attachments, revealing your sensitive data to steal money or sensitive information in your system. Such malware when activated could give cybercriminals what they wanted in the first place, to take control of your system, keep track of your keystrokes to keep a log, or accessing personal data leading to identity theft. It is always better not to share your username or password to anyone. Usually official emails from organizations like WHO would never ask you to visit other than their official website. So, its always better to be careful if you see anything suspicious about the email.
7. Avoid using unsecured, free, public WiFi hotspot or network
This decade we all have witnessed the explosion of free, public WiFi access and it has been a great relief and useful lifesaver for working professionals, mostly while traveling or these days if you are under lockdown in a hotel or you access free WiFi in a shopping center, retail outlets or other recreational places. Though this has given us more ways to stay connected and online, there are several risks associated with these connections. The biggest threat happens when a hacker with malicious intent positions himself between you and the WiFi connection point. You might very well be sending your information to the hacker. You might be inadvertently giving the hacker complete access to every piece of sensitive or non-sensitive information you are sharing via the Internet. It could be the company bank information, contracts, sensitive email or anything. Hackers may also use this unsecured network to spread malwares. So, its better to be careful in such situations. Using VPN, SSL connections, turning off sharing are some of the ways you can protect your system for attackers while using an unsecured network. But most importantly its always better to avoid using such a network if you have other options available.
8. Ensure that only authentic verified URLs are accessed
Never access websites that are not verified and not having an SSL certificate. Unsafe websites may intentionally or unintentionally spread malware, steal your information, and more. If you see an icon with the words “Secure” or “Verified,” it’s an indication that the site can be trusted as it has HTTPS security. Other safety features you can look at to verify can be the date since the website had its last malware scan. So, users need to be careful not to visit sites that are not authentic and verified.
9. Daily or weekly Backup of data in your system
Regular backup of data is one of the most critical ways and essential components of protecting your data. This is where you salvage what you might have lost in case of a system crash, hacker attack or any malware attack. Even though it is critical, most people do not take it seriously and ultimately suffer the consequences after any security incident or system breakdown. Its is always recommended to have a full backup enabling you to restore your PC to a previous state. You should also keep a copy of your data in the cloud (OneDrive, G Drive etc.) as another fail-safe mechanism using programs already provided with Windows and other operating systems.
10. Disable USB port and Bluetooth connectivity
It’s always better to disable USB ports and Bluetooth connectivity to prevent data from being stolen or leaked. This preventive measure is usually part of organizational policy on Endpoint Security Management to protect systems and sensitive data assets from external threats and unauthorized data access using USB device or bluetooth.
Below is the infographics with the Top 10 Security Tips for Work from Home.
Share this Image On Your Site
Want to know more about fortifying and safeguarding your organization’s critical assets. Talk to our cybersecurity experts!